 Shift from MDR, XDR, and AI SOC to Cyber Risk Operations
Shift from MDR, XDR, and AI SOC to Cyber Risk Operations
Your AI SOC is NOT ENOUGH.
Get Measurable Security Outcomes.
MDR, XDR, and AI SOCs optimize for alert efficiency. Cyber Risk Operations goes further; correlating massive signal volume with contextual business impact, control effectiveness, and attacker behavior to deliver measurable cyber risk reduction, not just faster response.
 The Shift to Adaptive Cyber Risk Operations
The Shift to Adaptive Cyber Risk Operations
Efficiency Closes Tickets.
Efficacy Kills CYBER RISK.
Threat efficiency is table stakes. Cyber Risk Operations aligns across Threat, Impact, Control, and Posture to continuously measure exposure, validate controls, and disrupt attack paths before impact.
 Beyond the AI SOC: Adaptive Cyber Risk Operations
Beyond the AI SOC: Adaptive Cyber Risk Operations
Stop Feeling Safe.
Start BEING PREPARED.
Passing audits doesn’t mean you’re protected.
Cyber Risk Operations replaces subjective safety with continuous situational awareness, so readiness is proven in real time, not assumed on paper.
Activity vs. Outcomes: From Threat Overload to Cyber Risk Control
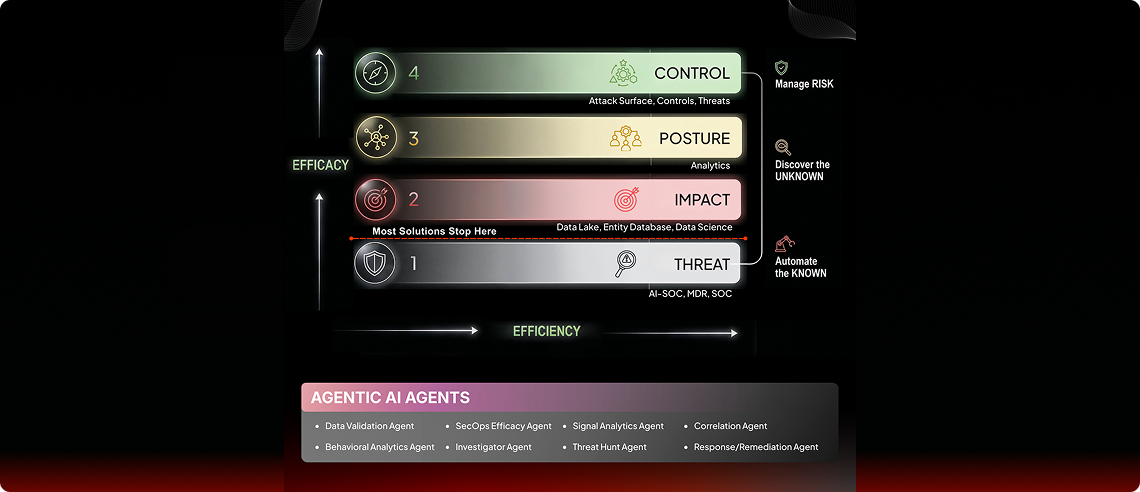
Netenrich Delivers Impactful Outcomes Across Four Dimensions
Most security platforms (SIEM, MDR, XDR, and AI SOC) operate almost entirely in the Threat dimension, optimizing speed and efficiency while lacking business ontology.
This is where most security operations plateau, no matter how much automation or AI is added.
Cyber Risk Operations moves security up the curve; from threat awareness to situational awareness beyond threat across Impact, Control, and Posture alignment, where real cyber risk is understood and managed.
Netenrich utilizes Agentic AI to bridge the gap between risk and operations, accelerating the evolution toward Adaptive Cyber Risk Security Operations.
Through the Resolution Intelligence CloudTM outcome-driven approach, it enables enterprises to not just feel safe, but to be prepared and resilient.
Prepared Isn’t a Buzzword. It’s Measurable.
See what happens when your SecOps shifts from reactive firefighting to proactive, intelligent defense with Netenrich.
The Four Dimensions of Cyber Risk Operations
Threat
From IOCs to Behavioral Coverage
Threat-focused security operations are not enough. Traditional SOCs reduce alerts to stay functional, at the cost of coverage.
Cyber Risk Operations intentionally expands visibility, ingesting and processing greater than 30x more threat signals and behaviors than traditional SIEM or MDR environments can handle.
Every security-relevant behavior is captured as a signal and correlated over time (not filtered away) creating complete behavioral visibility without overwhelming analysts.
Impact
From Alert Queues to Business Risk Prioritization
Seeing more signals only matters if you know which ones matter most.
Cyber Risk Operations applies the LIC Model (Likelihood × Impact × Confidence) to every correlated signal, converting raw activity into business-impact–aware risk decisions.
- Likelihood reflects adversary capability and attack stage
- Impact is derived from asset criticality (“Crown Jewels”) and loss potential (blast radius)
- Confidence adjusts prioritization based on signal fidelity and correlation strength
This replaces first-in/first-out alert handling with risk-weighted prioritization, ensuring teams address business exposure before technical noise.
Posture
From Reactive to Predictive
Most security failures happen without alerts, because the controls responsible for alerting are broken, missing, or misconfigured.
Cyber Risk Operations continuously validates posture at runtime, surfacing scenarios such as:
- Ghost assets missing security telemetry
- Attack surfaces and assets exposed to current global threats
- Control drift and non-permissive configuration changes
- Attack surfaces with exposures and vulnerabilities due to misconfigurations
- Risky but "authorized" behaviors that are risky
- Silent failures and abnormal behaviors that are risky
- Long and slow attacks over a 12-month period
This exposes the Illusion of Coverage, replacing assumed protection with evidence of what is actually working
Control
Align Attack Surface, Controls, and Threats (A.C.T)
Operating across Threat, Impact, and Posture enables continuous alignment of:
- Attack Surface (what exists and what matters)
- Controls (what is effective right now)
- Threats (what adversaries are actually doing)
This alignment projects attacker progression paths and allows teams to disrupt the kill chain before impact, not after breach.
Threat + Impact + Posture + Control = Cyber Risk Operations
Threat efficiency is table stakes. Situational awareness across all four dimensions is what reduces cyber risk.
The Security Outcomes
Your Business Demands
Security outcomes don’t improve by closing tickets faster. They improve when security can see more, understand more, and act with context.
Cyber Risk Operations delivers outcomes that are structural, measurable, and sustained; because it operates across Threat, Impact, Control, and Posture with continuous alignment - not in isolation.
Improvement in Detection Coverage
Coverage expands because Cyber Risk Operations does not suppress alerts or signals. It ingests and reasons over far more security data, revealing blind spots, drift, and attack activity others never see.
Reduction in Manual Workload
Agentic AI reasons over signals, context, and risk; so humans focus on judgment, investigation, and strategy, not queue processing.
Lower Total Cost vs. Building Internally
Autonomy reduces dependence on headcount growth, tool sprawl, and volume-based pricing models.
AI Autonomy Rate
Autonomous AI agents handle 98% of the operational noise and routine alert processing, which frees human analysts to focus exclusively on the 2% of strategic decisions that matter most.
Ghost Asset Rate
Data reveals that 18% of critical, revenue-generating servers are active on the network but missing security agents or telemetry, leaving them completely invisible to the SOC.
Incident Reduction
A customer experienced this outcome when tuning and automation reduced the volume of incidents requiring human intervention from 2,000 to under 10.
Cyber Risk Operations continuously aligns what you have, how it’s protected, and what's targeting it.
Cyber Risk and security efficacy improves quarter over quarter - even as environments and threats change.
The Illusion Of Coverage: Your Green Dashboard Is Lying
Feeling Safe Does NOT Mean Being Prepared.
Coverage only becomes meaningful when three things are understood together:
- But the most dangerous conditions rarely alert: control drift, missing telemetry, unmanaged assets, and risky “authorized”or unauthorized behavior.
- As environments change at machine speed, security assumptions expire just as fast. Infrastructure spins up and disappears, identities sprawl, configurations drift, and logs fail silently; without triggering an incident.
- Every change event can invalidate yesterday’s security assumptions. The result is the illusion of coverage: dashboards stay green, audits pass, alerts slow down, while preparedness quietly erodes underneath.
Bringing Coverage Back To Reality
Coverage only becomes meaningful when three things are understood together:
- What assets exist and which ones truly matter?
- Which controls are actually working right now?
- How attackers behave and progress over time?
By continuously correlating assets, controls, and attacker behavior, Cyber Risk Operations creates true situational awareness.
It shifts security leadership from “What alerts do we have?” to “Where are we exposed, how bad is it, and what must we act on first?”
From Threat Awareness to Situational Awareness
Threat awareness tells you what exists in the world. Situational awareness tells you what matters in your environment and what to do about it.
VULNERIBILITY EXPOSURE
Legacy tools bury you in "Critical" CVEs that don't matter. We isolate the threats that actually bankrupt you.
- Threat Awareness: A ‘Critical’ CVE is being actively exploited in the wild.
- Situational Awareness: This CVE targets your primary revenue engine where a compensating control is broken and lateral movement is wide open.
- The RiskOps Verdict: This needs immediate action. We prioritize this specific mitigation now, while deprioritizing the same CVE on isolated, non-critical assets that legacy tools would tell you to chase.
IDENTITY COMPROMISE SEQUENCE
Stop looking for "anomalous needles" in a haystack of false positives. Start killing the thread.
- Threat Awareness: A single anomalous sign-in alert for a privileged user.
- Situational Awareness: Our Agentic AI correlates that sign-in with silent mailbox rule creation and subsequent data movement over time.
- The RiskOps Verdict: This isn't an "anomaly", it is an active account compromise and a direct breach path. We escalate this as a high-impact action item immediately to disrupt the adversary before the data leaves the building.
DATA MOVEMENT
THE MDR NOISE: "THREAT AWARENESS"
- Signal: Large outbound data transfer.
- Problem: One of 10k alerts, ignored as "routine sync".
THE RISKOPS TRUTH: "SITUATIONAL READINESS"
- Signal: Identify that the transfer originates from a High-Value Asset.
Exposure: Agentic AI workforce detects that the transfer bypassed a DLP Policy (a Silent Control Failure) and maps it to historical Exfiltration Behavior.
The Math: Using the LIC Scoring Model, we calculate a high-confidence Risk score: Risk = (Likelihood × Impact) × Confidence.
THE ULTIMATUM: "IMMEDIATE NEUTRALIZATION"
- The Action: Treat as a High-Risk Exposure, not a ticket.
- The Action: Zero-Tolerance Neutralization. Our Agentic AI investigators autonomously gather evidence and initiate containment before material impact occurs, shifting your team from "Alert Factory" workers to Strategic Risk Supervisors.
LOW-AND-SLOW CREDENTIAL MISUSE
- Threat Awareness:Valid use of cloud credentials.
- Situational Awareness:The same long-lived credentials are accessed from multiple geographic regions over time, signaling credential compromise and lateral movement.
Action: Rotate credentials and disrupt the attack path before exfiltration.
CONTROL DRIFT
- THE MDR TRAP: No alert fired. In a legacy SOC, silence is treated as safety.
- THE SITUATIONAL TRUTH: A production log source silently stopped shipping data. This is a Silent Failure.
THE ULTIMATUM: Restore telemetry immediately before exposure compounds.
Math: Risk = (Likelihood x Impact) x Confidence. When Confidence drops, Risk skyrockets
AUTHORIZED BUT RISKY BEHAVIOR
- MDR BLIND SPOT: Admin action detected. Marked "Authorized"
- SITUATIONAL TRUTH: Cloud Admin spinning up infra outside Change Control. This is Shadow Ops.
Action: Trigger validation and enforce policy before abuse escalates.
SEVERITY WITHOUT CONTEXT
- Threat Awareness: High-severity alert triggered.
- Situational Awareness: The activity targets a low-impact endpoint and matches the user’s role, while a medium-severity signal elsewhere targets a crown-jewel system with weak controls.
Action: Deprioritize safely. Escalate what actually threatens the business.
Rethinking Cyber Risk for a World That Never Stands Still
Traditional security operations are designed to respond to incidents. They optimize for alert handling, ticket closure, and after-the-fact investigation.
Cyber Risk Operations is designed to manage cyber risk continuously, not just react to events.
Are you prepared right now, and can you prove it?
Cyber risk doesn’t live in tools or alerts, it lives in your environment.
Netenrich continuously maps your assets (attack surface), identities, controls, and threats into a living operational model, giving security teams a single, trusted view of what exists, what’s protected, and where real risk is emerging, right now.
From Your Environment Data to Operational Truth
- Unified Data: Security telemetry across cloud, identity, endpoint, network, SaaS, and applications is normalized into a single operational view of the customer environment.
- Contextual Risk Modeling: Signals are evaluated in context (asset criticality, control coverage, configuration posture, and attacker behavior) so risk is understood, not just detected.
- Continuous Risk Reasoning: Analytics continuously assess exposure, drift, and attacker movement as environments and threats evolve, eliminating blind spots between reviews.
- Actionable Workflows: Insights flow directly into validation, remediation, or escalation workflows; prioritized by real risk, not alert volume.
- Authoritative Operational Truth: Integrations enrich and act, but the environment model remains the trusted source for what exists, what’s protected, and what requires action; right now.
Netenrich Autonomous Security Operations unify AI, data, and human expertise into one continuously improving security model.
A Digital Workforce of AI Agents for Adaptive Cyber Risk Operations
Netenrich enables Agentic AI-based, coordinated systems of autonomous security agents that handle operational work at machine speed, while humans focus on high-impact decisions.
Data Validation Agent
Ensures log integrity, detects silent failures, validates parsing health.
Threat Modelling Agent
Continuously validates detection pipelines and SOC health.
Signal Analytics Agent
Analyzes historical data to identify hidden patterns and slow-brewing attacks that real-time rules miss.
Correlation
Agent
Stitches signals into ACT-driven incident chains using LIC scoring.
Behavioral Analytics Agent
Establishes baselines for user and asset behavior to identify high-risk deviations and anomalies.
Investigator
Agent
Automates deep investigation, maps kill chains, drafts verdicts.
Threat Hunt
Agent
Proactively hunts unknown threats using behavior and model context.
Response/Remediation Agent
Executes automated playbook actions to instantly neutralize threats and isolate compromised assets.
The Blueprint For Readiness. How We Quantify Risk.
Automate The Known: Kill The Alert Factory
Cyber Risk Operations treats alerts as signals, not work items
Agentic AI continuously ingests, correlates, and reasons over tens of thousands of behaviors per day, handling known patterns, repeat conditions, and routine investigations automatically.
This allows security teams to see everything without manually touching everything and focus human effort where judgment is required.
-
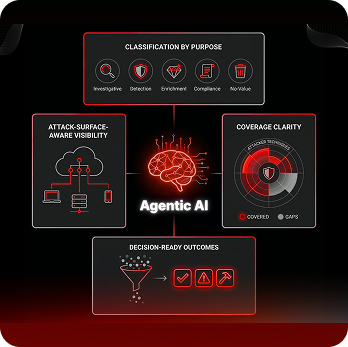
Classification by purpose: Log sources are categorized by investigative value, detection value, enrichment value, compliance value, or no-value; reducing cost without reducing coverage.
- Attack-surface–aware visibility: Alert/Signals are mapped to real attack surfaces (identity, endpoint, cloud, SaaS, network, hypervisor), not treated as generic events.
- Coverage clarity: Detection coverage is mapped to attacker techniques, and gaps are made explicit before adversaries find them.
- Decision-ready outcomes: Raw events are transformed into a small set of high-confidence action items through continuous correlation and optimization.
Discover The Unknown: Hunt The Unseen. Eliminate The Stealth.
Not all risk announces itself. Cyber Risk Operations goes beyond static detection rules by applying behavioral analytics and continuous threat hunting across extended time horizons, uncovering scenarios that evade traditional security operations.
We don't wait for alerts. We weaponize the ACT Framework (aligning Attack Surface, Controls, and Threats) to actively search for the scenarios legacy solutions miss:
- Low-and-Slow Execution: We map multi-stage kill chains across months of data, not just hours.
- Access Hijacking: We expose the abuse of legitimate access before it turns into a headline.
- Ghost Techniques: We find the emerging threats that evade static signatures by hunting behavioral intent.
- And more such scenarios
Unknown risk isn't a problem, it’s the target. We replace subjective feelings of safety with mathematical Situational Awareness.
- Posture-driven threat discovery: Posture weaknesses are directly mapped to relevant threat techniques and adversary behaviors.
- Multiple hunting strategies: Hunting is continuous and multi-modal; combining behavioral analytics, threat intelligence, exposure analysis, and signal correlation.
- Risk register with intent: A living register of the most critical exposures across identity, endpoint, cloud, SaaS, network, and infrastructure; prioritized with clear remediation guidance.
Manage Risk: Align Attack Surface, Controls, and Threats (A.C.T.): and Adapting to Drift
Coverage is not assumed, it’s proven.
As environments and threats change, yesterday’s controls drift out of alignment.
Cyber Risk Operations continuously validates:
- What exists: assets, identities, dependencies, and attack surface
- What’s actually working: control effectiveness and telemetry health
- What’s targeting you: active and emerging attacker behavior
This alignment ensures actions are prioritized by business impact and exposure, not generic severity or alert volume.
Cyber Risk moves from periodic review and reactive response to continuous measurement, reasoning, and adaptation.
The Core Engine:
The RiskOps DNA. Move Beyond the Illusion of Coverage.
Cyber Risk Operations works because it isn’t a toolset or a service wrapper.
It’s a disciplined operating model, engineered to deliver sustained cyber risk outcomes, even as environments, attack surfaces, and threats continuously change.
Why Customers Choose Us
- Efficacy First: Security measured by risk reduction, not alert throughput or ticket volume.
- Measurable Outcomes: Readiness that can be quantified, tracked, and demonstrated over time; not inferred from dashboards.
- Continuous Adaptation: Defenses evolve as business velocity, attack surfaces, and adversary behavior change.
Cross Discipline Team DNA
- SRE and Digital Ops DNA
Continuous validation, reliability checks, and feedback loops are built in to prevent drift. - Security Engineering Rigor
Detections, controls, and response logic are engineered systems, not ad hoc rules. - Data Science Discipline
Prioritization is driven by risk-based scoring, not static High/Medium/Low labels.
Engineering Approach to RiskOps
- Data Engineering at Scale: High-fidelity telemetry and long-horizon signal retention across environments.
- Detection and Behavioral Engineering: Coverage aligned to real attacker behavior, not just known signatures.
- Quantified Response Engineering: Actions driven by likelihood, impact, and confidence, not alert volume.
Most vendors address one dimension in isolation. Cyber Risk Operations works because all three pillars operate on the same data, context, and decision logic, continuously.
From “Feeling Safe” to “Being Prepared”
Is your current provider sending you work to triage, or outcomes that reduce risk?
Compliance checks boxes. Cyber Risk Operations proves readiness.If your security model still relies on static assumptions in a dynamic world, drift is inevitable.
Let’s assess how prepared your organization actually is and what continuous readiness looks like in practice.
Delivering Real-world
Outcomes for Global Enterprises
Don’t take our word for it – hear directly from our customers about how we transformed their security operations.
“Netenrich gave us clarity we didn’t have before. By collapsing dozens of disconnected workflows into a small number of risk-driven operating paths and materially expanding our detection coverage, we moved from managing alerts to managing risk. We now operate with far greater confidence and precision.”
Kumar Palaniappan
CISO, Citrix (Cloud Software Group)
“With Netenrich and Google SecOps, our team focuses on what actually matters — meaningful investigations and risk decisions, not chasing noise. We can now explain our security posture clearly to leadership and show how our controls, detections, and response align to business risk.”
Harsh Jha
CTO, Nuvama Group
“Netenrich didn’t just solve today’s problems. They helped us adopt an operating model that scales as our environment changes. Our security operations are now adaptive, resilient, and built for long-term risk management.”
CISO
Healthcare Organization
Success Stories & Resources


Case Study
Citrix and Cloud Software Group Transforms Security Operations with Netenrich Adaptive MDR
![Digital Marketing Banner[10]](https://netenrich.com/hs-fs/hubfs/Digital%20Marketing%20Banner%5B10%5D.png?width=800&height=421&name=Digital%20Marketing%20Banner%5B10%5D.png)
![Regional Bank Banner[88]](https://netenrich.com/hs-fs/hubfs/Regional%20Bank%20Banner%5B88%5D.png?width=800&height=421&name=Regional%20Bank%20Banner%5B88%5D.png)
![Healthcare Banner[47]](https://netenrich.com/hs-fs/hubfs/Healthcare%20Banner%5B47%5D.png?width=800&height=421&name=Healthcare%20Banner%5B47%5D.png)









